Students can access the CBSE Sample Papers for Class 10 Computer Applications with Solutions and marking scheme Set 2 will help students in understanding the difficulty level of the exam.
CBSE Sample Papers for Class 10 Computer Applications Set 2 with Solutions
Time Allowed: 2 Hours
Maximum Marks: 50
General Instructions:
- This Question Paper has 5 Sections A-E.
- All Questions are compulsory. However, internal choices have been provided in some of the questions.
- Section A has 12 questions carrying 1 mark each.
- Section B has 7 Short Answer (SA-I) type questions carrying 2 marks each.
- Section C has 4 Short Answer (SA-II) type questions carrying 3 marks each.
- Section D has 1 Long Answer (LA) type question carrying 4 marks.
- Section E has 2 Source based /Case-based /Passage based Questions carrying 4 marks each.
SECTION – A (12 Marks)
(All questions are compulsory)
Question 1.
POP 3 stands for _____________ [1]
(a) Post Office Packet 3
(b) Post Office Protocol 3
(c) Post Office Period 3
(d) Post Office Point 3
Answer:
(b) Post Office Protocol 3
Explanation:
POP is Post office protocol, a protocol used for mail transfers.
Question 2.
Web address of the national portal of India is? [1]
(a) India.gov.in
(b) GOI.gov.in
(c) ncert.nic.in
(d) None of the these
Answer:
(a) India.gov.in
Explanation:
The portal of national portal of Government of India is: India.gov.in
Question 3.
T in <HTML> stands for [1]
(a) Text
(b) Tag
(c) Tiled
(d) None of these
Answer:
(a) Text
Explanation:
HTML stands for hypertext mark up language. A language to design web pages.
![]()
Question 4.
The website of an electricity supply company which allows its customers to pay bills online is an example of _________ [1]
(a) e-Business
(b) e-Mail
(c) e-Governance
(d) e-Learning
Answer:
(a) e-Business
Explanation:
Electricity supply bill payment is e-Business. As it involves business transactions.
Question 5.
Which of the following tags is used to link the URL? [1]
(a) <hyperlink>
(b) <link>
(c) <a>
(d) < style >
Answer:
(C) <a>
Explanation:
The <a href=”link” > is used to link a URL to a page object.
Question 6.
“href” is an attribute of_______Tag [1]
(a) <body>
(b) <a>
(c) <html>
(d) <img>
Answer:
(C) <html>
Explanation:
The href attribute is used to specify the link which takes the user to the target.
Question 7.
The_________tag is used to show an image in a HTML page [1]
(a) alt
(b) text
(c) alternate
(d) img
Answer:
(d) img
Explanation:
The <img src=”file”> is used to insert an image in a web page.
Question 8.
Which attribute does not come in <HR> tag? [1]
(a) Size
(b) Color
(c) Width
(d) Length
Answer:
(d) Length
Explanation:
The size, color, and width are used to specify the thickness, color, and percentage of the rule.
![]()
Question 9.
In HTML <DL> tag is used to create: [1]
(a) Tables
(b) Lists
(c) Definition lists
(d) None of these
Answer:
(c) Definition lists
Explanation:
The <DL> tag creates a definition list.
Question 10.
Using someone else’s Twitter handle to post something will be termed as_________ [1]
(a) Fraud
(b) Identity theft
(c) Online stealing
(d) Violation
Answer:
(b) Identity theft
Explanation:
Since someone else’s identity is used for posting something without his/her consent, it is a case of Identity theft.
Questions No-11 to 12 are Assertion and Reason types. Each question consists of two statements, namely, Assertion (A) and Reason (R). Select the most suitable option considering the Assertion and reason.
Question 11.
Assertion (A): Email is one of the applications of the Internet to send data and messages faster.
Reason (R): Email requires both the sender and receiver to be online.
(a) Both Assertion (A) and Reason (R) are true and Reason (R) is a correct explanation of Assertion (A).
(b) Both Assertion (A) and Reason (R) are true but Reason (R) is not a correct explanation of Assertion (A).
(c) Assertion (A) is true and Reason (R) is false.
(d) Assertion (A) is false and Reason (R) is true.
Answer:
(c) Assertion (A) is true and Reason (R) is false.
Explanation:
Both sender and receiver need not be online, as the receiver may see the mailbox later.
Question 12.
Assertion (A): CSS helps in applying formats to <HTML> elements.
Reason (R): CSS files contain formatting attributes and properties for the HTML tags used in the HTML page
(a) Both Assertion (A) and Reason (R) are true and Reason (R) is a correct explanation of Assertion (A).
(b) Both Assertion (A) and Reason (R) are true but Reason (R) is not a correct explanation of Assertion (A).
(c) Assertion (A) is true and Reason (R) is false.
(d) Assertion (A) is false and Reason (R) is true.
Answer:
(a) Both Assertion (A) and Reason (R) are true and Reason (R) is a correct explanation of Assertion (A).
Explanation:
A cascading style sheet stores styling information of tags and hence can be used for applying formats to HTM elements.
![]()
SECTION – B (14 Marks)
Question 13.
What is the difference between chat and email? [2]
Answer:
| Chat | |
| (1) Chat is a type of online communication in which users type messages back and forth in real time. | (1) Email is a system for sending and receiving electronic messages, typically across the internet. |
| (2) Chat is often used for informal communication between friends or colleagues. | (2) Email is more commonly used for formal or business-related correspondence. |
Question 14.
Give two addresses of most commonly used e-Learning sites.
OR
What social impact does e-Governance have on society? [2]
Answer:
www.khanacademy.com
http://www3schools.com/
OR
(a) Efficiency of administration has increased.
(b) Reduced cost.
(c) Corruption has reduced.
(d) Fast processing.
Question 15.
Write two advantages of 4G over 3G Mobile communication technologies in terms of speed and services. [2]
Answer:
Speed: 4G offers a speed of more than 10 Mbps while 3G around 3 Mbps.
Services: It can prioritize services to offer a flawless performance.
Example:
VoIP is prioritised over other data to offer flawless calling experience
Question 16.
What is privacy in e-Commerce?
OR
Name five common intellectual property rights. [2]
Answer:
Privacy in e-Commerce means the protection of privacy of all the parties involved in trading through e-Commerce.
OR
Copyrights, patents, trademarks, trade secrets, industrial designs.
Question 17.
Identify the errors and write the correct HTML code [2]
(a) <BODY background=”red” >
(b) <FONT type=”arial”>
Answer:
(a) <BODY bgcolor=”red”> #use bgcolor instead of background
(b) <FONT face=”arial”> #use face instead of type
![]()
Question 18.
Match the tags in column A with the tag/attribute list given in column B:
| Column A | Column B |
| (a) HR | (i) bgcolor |
| (b) body | (ii) face |
| (c) P | (iii) size |
| (d) font | (iv) align |
OR
Mention any two attributes of <img> tag [2]
Answer:
(a) HR – (iii) size
(b) Body – (i) bgcolor
(c) P – (iv) align
(d) Font – (ii) face
OR
(a) Width
(b) Height
Question 19.
Which tag/attributes of HTML are used to: [2]
(a) Insert a picture in a web page.
(b) Insert an empty line in the web page.
Answer:
<IMG> Tag
<BR> OR <P> Tag
SECTION – C (12 Marks)
Question 20.
Explain CSS inline style. [3]
Answer:
Inline style sheet is a term that refers to style information being applied to the current element.
Example:
<!DOCTYPE html> <html> <head> <title> Learning HTML </title> </head> <body> <p style="font-size: xx-large; color:maroon; text-align:center; border: groove 5px orange"> Learning HTML </p> <p style="font-size: x-large; color:green; text-align:right; border:ridge 3 px maroon"> Learning HTML </p> <p style="font-size: medium; color:navy; text-align:left; border: dashed 4 px green"> Learning HTML </p> </body></html>
Question 21.
Write the HTML code for the following to appear one after the other: [3]
(a) A small heading with the words, “HAPPY BIRTHDAY”
(b) A horizontal rule across the page
(c) A large heading with the one word,” CATHY”
(d) A medium-sized heading with the words, “May 10 2019”
(e) Another horizontal rule
Answer:
<html> <headxtitle> INVITE </titlex/head> <body> <h5> HAPPY BIRTHDAY </h5> <hr> <hl> CATHY </hl> ' <H3> May 10 2019 </h3> <hr> </body> </html>
Question 22.
Write HTML code for the following:
To provide hyperlink to a website “http://www.cbse.nic.in”
OR
Write HTML code to display the following list with red background. [3]
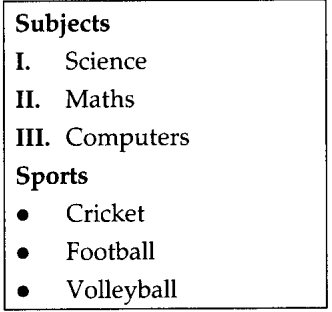
Answer:
<html> <head> <title> link </title> </head> <body> <a href="http://www.cbse.nic.in">www. cbse.nic. in </a> </body> </html>
OR
<htmi>
<head>
<title> My Subjects </title>
</head>
<body bgcolor =”red”>
<h2> Subjects </’h2>
<ol type=”I”>
<li> Science </li>
<li> Maths </li>
<li> Computers </li>
</ol>
<h2> Sports C/h2>
<UL>
<Li> cricket </li>
<Li> Football </ii>
<Li> Volleyball </li>
</UL>
</body>
</html>
Question 23.
What is software piracy? [3]
Answer:
Software piracy is any attempt to break the license terms of a piece of software. This includes downloading and using a program without paying for it, as well as buying, selling or giving away illegitimate copies of a game or any other piece of software. It could mean extracting code from a program, or modifying it without permission in order to do something that the developers did not wish you to do.
When you buy software, music or films legally, copyright law forbids us from :
- Giving a copy to a friend.
- Making a copy and then selling it.
- Using the software on a network (unless the license allows it, eg it is a business license).
- Renting the software without the permission of the copyright holder.
The practice of copying software is a serious problem in some countries. Copying music, films and software illegally means that there is less money available to pay the writers, developers and artists.
![]()
SECTION – D (4 Marks)
Question 24.
Write the HTML code to design the below shown form: considering the specifications as given below:
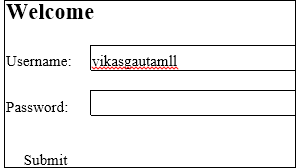
OR
Write the code to generate the following HTML table [4]
| Column 1 | Column 2 | Column 3 |
| Row 1 Cell 1 | Row 1 Cell 2 | Row 1 Cell 3 |
| Row 2 Cell 2 | Row 2 Cell 3 | |
| Row 3 Cell 1 | ||
Answer:
HTML code to generate the above form:
<!DOCTYPE html> <html> <head> <title>Page Title</title> </head> <body> <h2>Welcome </h2> <<Form> <P> <label>Username: cinput type="text" /></label> <P> <label>Password: <input type="password" /></label> </p> <P> <input type="submit">submit</button> </p> «/Form» </body> </html>
OR
<!DOCTYPE html> <html> <ti,tle>HTML Table Background</title> </head> <body> <table border = "1" bordercolor ="brown" bgcolor = "pink"> <tr> <th>Column l</th> <th>Column 2</th> <th>Column 3</th> </tr> <tr> <td rowspan = "2">Row 1 Cell K/td> <td>Row 1 Cell 2</td> <td>Row 1 Cell 3</td> </tr> <tr> <td>Row 2 Cell 2</td> <td>Row 2 Cell 3</td> </tr> <tr> <td colspan = ”3">Row 3 Cell l</td> </tr> </table> </body> </html>
SECTION – E (8 Marks)
Question 25.
Sunaina is working with a publication company. Help her in providing certain solutions for the following issues:
(a) Company secretary sends a link to Manager which contains important company files. What should he do in order to access the files? [1]
Answer:
Download the files from the link.
(b) Some writers want to search material on the web for which they want to use open source web browsers. Suggest them names of two web browsers. [1]
Answer:
Two web browsers are: Mozilla firefox, Opera.
(c) Some employees are downloading material from the web. Which protocol they are using for such downloads? [1]
Answer:
They are using the FTP: File Transfer Protocol.
(d) Sunaina wants to hold an online meeting with the company’s client such that she can interact as well as see them. Which web service should she avail? [1]
Answer:
(d) Video conferencing
Question 26.
Suman is new user of the internet and doesn’t not much about the do’s and dont’s and applications of the web. Help her in following cases:
(a) She got multiple useless mails from same source advertising about a product. What are these? [1]
Answer:
These are called spam.
(b) She posted some post about someone else then her friend asked that there is not right to post about someone else without his/her knowledge. This feature come under in which term? [1]
Answer:
Netiquettes
(c) She made her assignment to copy the matter from internet word for word. What is this? [1]
Answer:
Plagiarism
(d) Give her any two tips on how she can protect her system. [1]
Answer:
(i) Do not give Email ID to all.
(ii) Disconnect from internet when not in use.
![]()